
Help customers break the safety data island, remove safety data pollution, open up the SDL safety development engine tool chain,
Further magnify the real value of the security engine, tamp the security data foundation,
and help enterprises achieve a virtuous business cycle of DevSecOps.
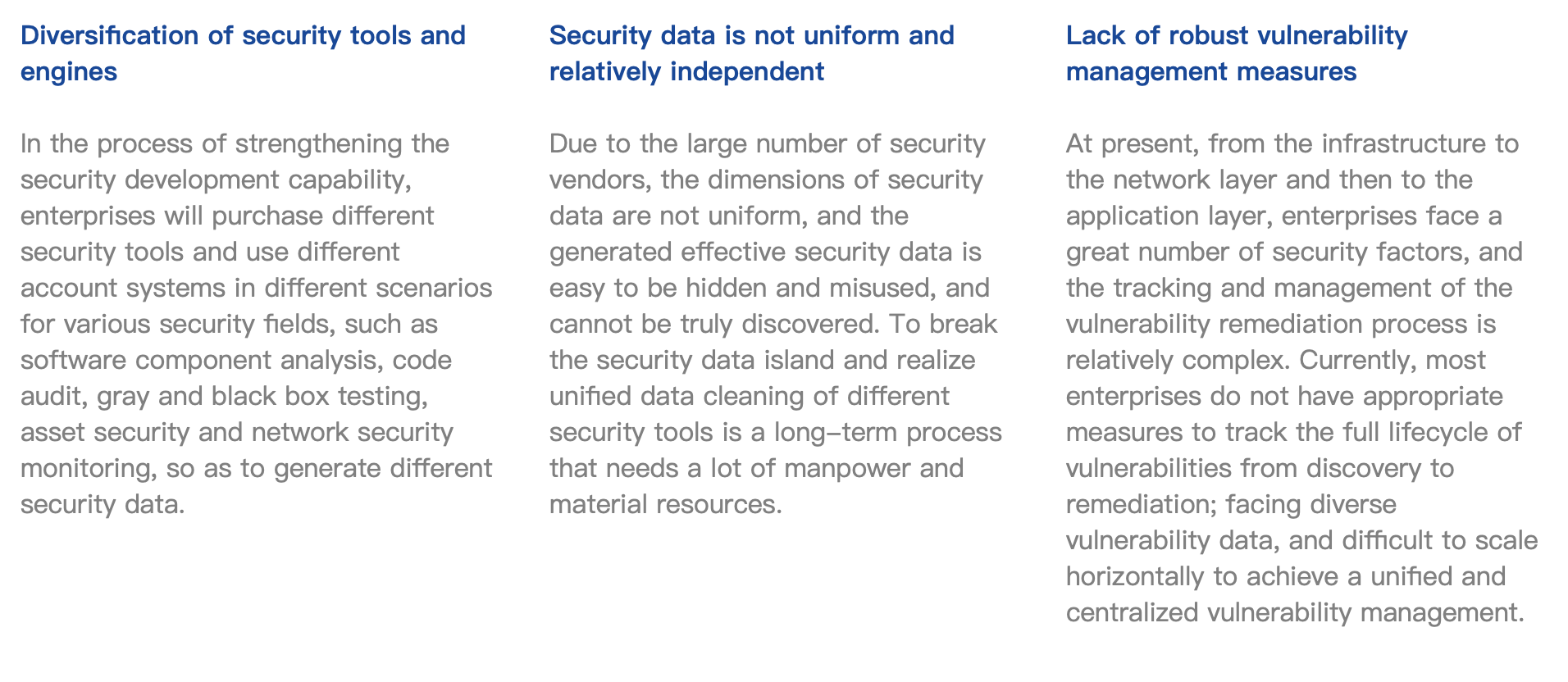
Diversification of security tools and engines In the process of strengthening the security development capability, enterprises will purchase different security tools and use different account systems in different scenarios for various security fields, such as software component analysis, code audit, gray and black box testing, asset security and network security monitoring, so as to generate different security data. |
Security data is not uniform and relatively independent Due to the large number of security vendors, the dimensions of security data are not uniform, and the generated effective security data is easy to be hidden and misused, and cannot be truly discovered. To break the security data island and realize unified data cleaning of different security tools is a long-term process that needs a lot of manpower and material resources. |
Lack of robust vulnerability management measures At present, from the infrastructure to the network layer and then to the application layer, enterprises face a great number of security factors, and the tracking and management of the vulnerability remediation process is relatively complex. Currently, most enterprises do not have appropriate measures to track the full lifecycle of vulnerabilities from discovery to remediation; facing diverse vulnerability data, and difficult to scale horizontally to achieve a unified and centralized vulnerability management. |
Project Management Comprehensive perspective and monitoring of project health, security status, and vulnerability status. |
Data Analysis Output unified aggregated report analysis, data analysis results support customization, and continuous tracking of vulnerability KPI indicators. |
Vulnerability Management Centralized processing of all kinds of vulnerability data, and establish a unified circulation tracking cycle. At the same time to achieve the third party penetration test, and mobile terminal report data fusion. |
Data dimensionality and visualization Multi-dimensional data drilling, processing and presenting security data information from roles, permissions, and security engine dimensions. |
Establish a sound loop-loop of vulnerability management Aiming at multiple dimensions of vulnerability management, a complete security vulnerability management chain is established to provide a complete closed loop for the whole process of vulnerability detection and repair. |
The security engine is centrally managed Realize the single sign-on of the multi-engine account system, without the need to repeatedly manage the multi-system account under the multi-engine capability. |
Pivottables are much clearer The multi-dimensional data is fused to achieve unified management, while international standard security products can be docked to introduce unified analysis and tracking of security data. |
The security engine is flexibly configured Components safety, white box test, gray box test, black box test and container safety multiple engines, support flexible selection and free combination, no additional auxiliary development work. |
Company Name: Shanghai Jingan Information Technology Co., LTD
Email:info@easmcn.com

Official Accounts

Mini Programs