
When an emergency security breach or 0-day security breach occurs on the Internet, provide customers with accurate Web asset location capabilities, greatly improving the customer's emergency response speed; when an emergency security incident occurs in the customer's business system, provide remote and on-site in-event suppression and post-event processing and other security support to help customers deal with security incidents quickly and reduce the impact of security incidents on business.
Based on the threat intelligence system of Jingan Technology, aiming at the emergency security vulnerabilities and 0day vulnerabilities of the Internet, it can accurately identify the security risks of customers' web business systems, quickly locate risk assets, improve emergency response capabilities, and avoid security incidents.
Comprehensively investigate and clean up malicious programs such as viruses, Trojans, worms, and backdoors in the system, as well as malicious pages such as Webshells, dark links, black links, hanging horses, and sensitive content in Web sites.
Through comprehensive analysis of system, application and other logs, combined with the loopholes in the system and application, find out the hacker intrusion path.
Establish and improve the emergency standard process to ensure that the emergency response process meets the standard requirements, and effectively improve the user's ability to deal with emergency response events. Position risk assets, improve emergency response capabilities, and avoid security incidents.
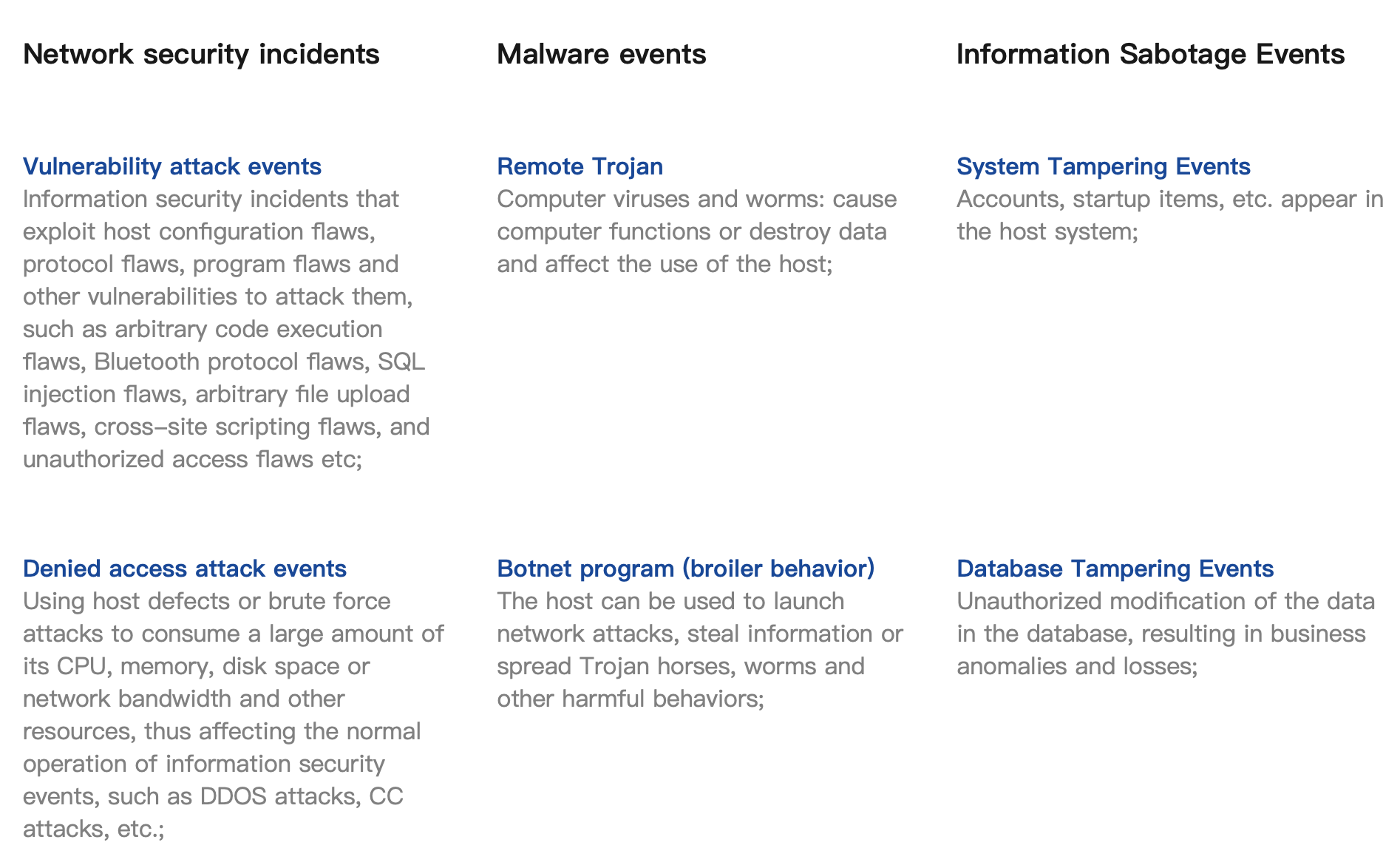
Network security incidents |
Malware events |
Information Sabotage Events |
Vulnerability attack events Information security incidents that exploit host configuration flaws, protocol flaws, program flaws and other vulnerabilities to attack them, such as arbitrary code execution flaws, Bluetooth protocol flaws, SQL injection flaws, arbitrary file upload flaws, cross-site scripting flaws, and unauthorized access flaws etc; |
Remote Trojan Computer viruses and worms: cause computer functions or destroy data and affect the use of the host; |
System Tampering Events Accounts, startup items, etc. appear in the host system; |
Denied access attack events Using host defects or brute force attacks to consume a large amount of its CPU, memory, disk space or network bandwidth and other resources, thus affecting the normal operation of information security events, such as DDOS attacks, CC attacks, etc.; |
Botnet program (broiler behavior) The host can be used to launch network attacks, steal information or spread Trojan horses, worms and other harmful behaviors; |
Database Tampering Events Unauthorized modification of the data in the database, resulting in business anomalies and losses; |
Network Scanning Attack Events Use network scanning tools to obtain information security incidents caused by host network configuration, ports, services, existing vulnerabilities and other characteristics; |
Mining program Causes a lot of consumption of host resources, and the business system cannot work normally; |
Web Page Tampering Events The website pages are implanted with malicious content such as viruses, gambling, pornography, gambling, etc.; |
Emergency Security Breach Response For the frequent and urgent security vulnerabilities on the Internet, we provide the ability to locate them quickly through feature library identification. For example: Struts2, Weblogic, Jboss remote execution command vulnerability, Java deserialization vulnerability, Jenkins arbitrary file reading vulnerability, etc. |
WebShell Program Attackers can obtain system information and control the host through WebShell; |
Information Leakage Incident Information leakage incidents caused by factors such as misoperation, software and hardware defects, or electromagnetic leakage; |
Information Destruction Events Information destruction events caused by the exposure of sensitive, personal privacy and other information to unauthorized persons. |

Through emergency response services, we help customers understand their own security status, and conduct in-depth and comprehensive analysis of security issues faced by enterprises.
Through emergency response training, help customers master the key processes, analysis methods and experience skills of emergency response, and improve their own ability to deal with emergency response events.
Help customers establish and improve emergency response systems, improve various emergency management processes and management methods, ensure the availability of emergency management methods, reduce the cost of enterprise emergency response and disposal, and improve enterprise efficiency.
Company Name: Shanghai Jingan Information Technology Co., LTD
Email:info@easmcn.com

Official Accounts

Mini Programs