
Provide source code security assessment, blue army assessment services, security vulnerability assessment and APP security assessment services for client business systems, discover security vulnerabilities and hidden dangers of client application systems and their environments, and effectively reduce security risks of client application systems by guiding security rectification, to ensure the safe and stable operation of the business system.
In the process of development and testing, provide source code interactive detection capabilities for customer business system function modules to detect common web security vulnerabilities and conventional business logic vulnerabilities; provide source code auditing services through the combination of manual labor and tools, from the source code level Identify business security risks.
Conduct a comprehensive and in-depth security test on the target system from the attacker's perspective, oriented to obtain data and obtain permissions. Use composite security testing methods, such as vulnerability scanning, vulnerability checking, penetration testing, and vulnerability verification. Accurately locate and expose business risk points and provide remediation suggestions. The scope of services includes: Web application testing, operating systems, interface programs, etc.
Use vulnerability scanners to detect security vulnerabilities in business systems and provide vulnerability assessment reports and repair suggestions.
On mobile APP programs from the perspective of attackers, discover possible security flaws, and provide security test reports and improvement suggestions. Including: Android, IOS, applet, etc.
Security assessment of ATM machines, self-service terminals, cameras, handheld terminals, set-top boxes, and other equipment.
Based on the security vulnerability assessment results, we formulate security hardening plans to assist customers in completing security hardening.
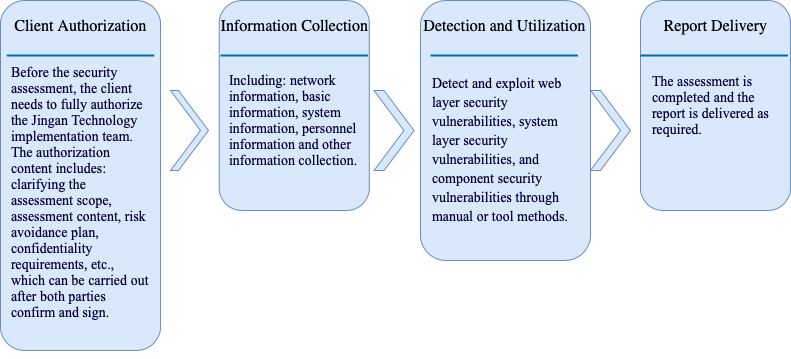
The Jingan Technology service team are active in the major SRC rankings and have evaluated hundreds of companies. They have comprehensive technologies and rich experience in vulnerability mining. While digging in-depth vulnerabilities, they empower customer security teams and improve their security technical capabilities.
Provide all-round security assessment technologies such as business security, system security, code security, network security, data security, and third-party security, comprehensively assess the security status of customer business systems, and improve security defense capabilities.
Provide normalized operation capabilities after the customer's business system goes online, including asset risk monitoring, vulnerability repair status management and control, security vulnerability threat intelligence, etc., to improve security operation capabilities.
Company Name: Shanghai Jingan Information Technology Co., LTD
Email:info@easmcn.com

Official Accounts

Mini Programs